□ 개요
o MS Exchange Server에서 원격 코드 실행이 가능한 취약점
□ 설명
o Microsoft Exchange Server에서 발생하는 SSRF(Server-Side Request Forgery) 취약점(CVE-2022-41040)
o Microsoft Exchange Server에서 발생하는 원격 코드 실행 취약점(CVE-2022-41082)
□ 영향을 받는 제품
o Microsoft Exchange Server 2013, 2016 및 2019
□ 해결 방안
o IIS Manager를 통해 차단 룰 적용
1. IIS Manager -> Default Web Site -> Autodiscover -> URL Rewrite를 클릭

2. Actions 창에서 Add Rules 클릭

3. Request blocking을 선택하고 OK 버튼 클릭
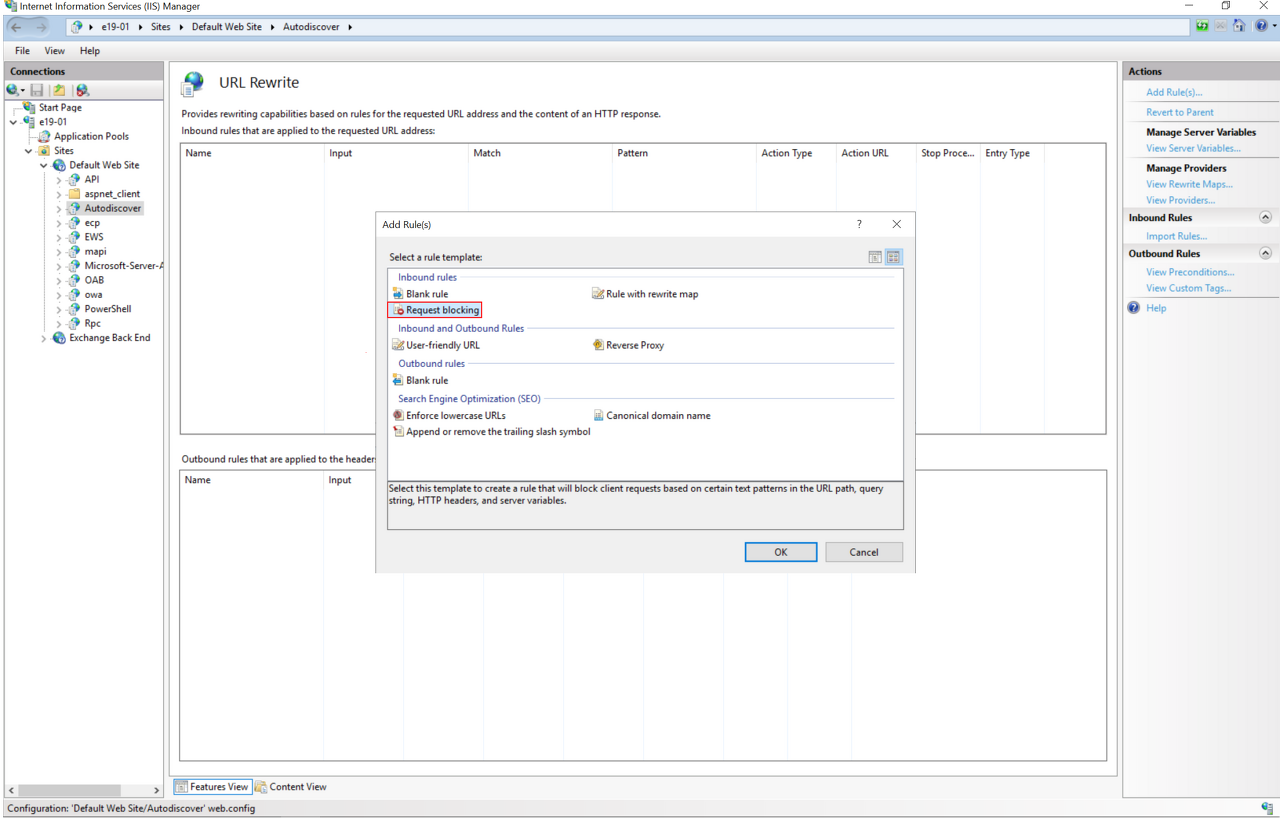
4. “.*autodiscover\.json.*\@.*Powershell.*” 문자열 입력(쌍따옴표 제외) 후 OK 버튼 클릭
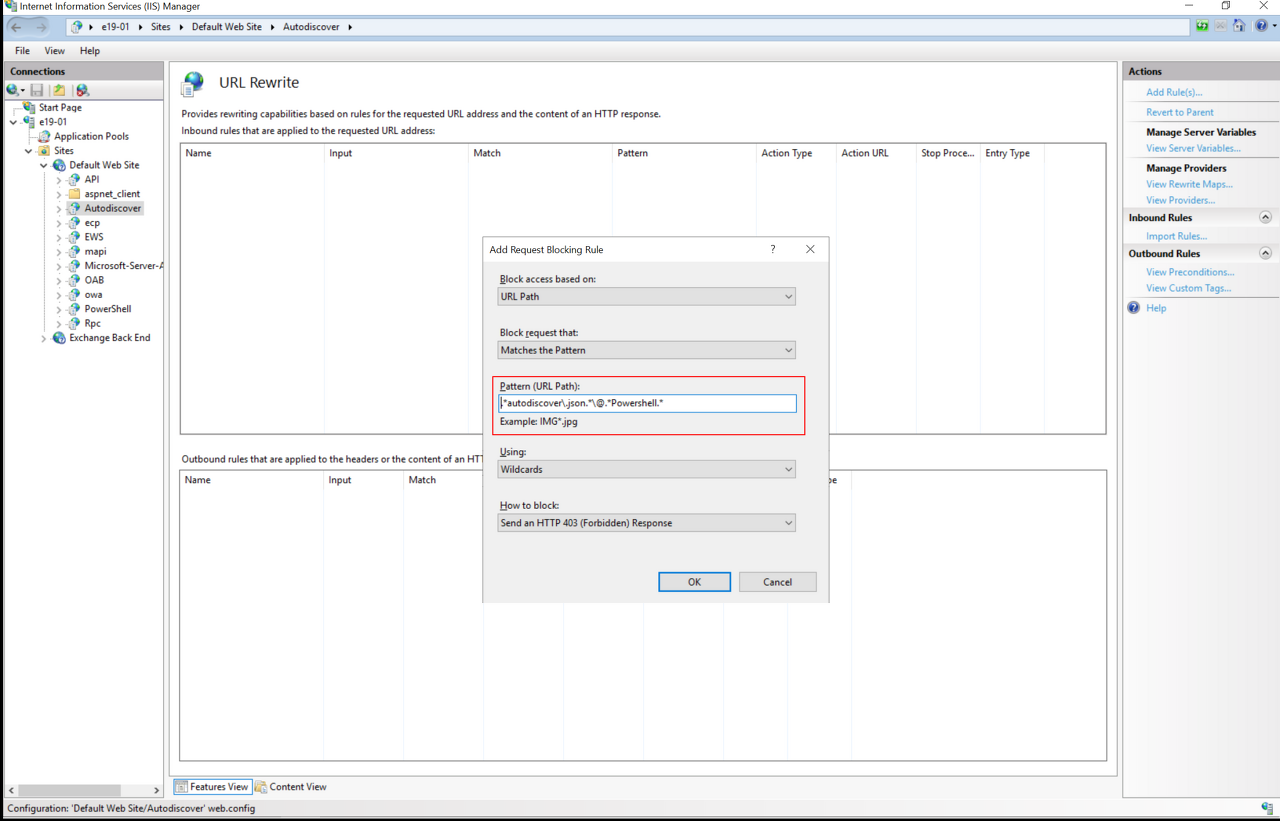
5. 룰을 펼쳐 “.*autodiscover\.json.*\@.*Powershell.*” 패턴이 적용된 룰을 선택 후 Conditions 창 아래 Edit 클릭

6. Condition Input에 {URL}을 {REQUEST_URI}로 변경

o 원격 파워쉘 포트 차단
- HTTP : 5985
- HTTPS : 5986
Customer Guidance for Reported Zero-day Vulnerabilities in Microsoft Exchange Server
October 2, 2022 updates:
- Added to the Mitigations section: we strongly recommend Exchange Server customers to disable remote PowerShell access for non-admin users in your organization. Guidance on how to do this for single user or multiple users is here.
- Updated Detection section to refer to Analyzing attacks using the Exchange vulnerabilities CVE-2022-41040 and CVE-2022-41082.
September 30, 2022 updates:
- Added link to Microsoft Security blog in Summary.
- Microsoft created a script for the URL Rewrite mitigation steps and modified step 6 in the Mitigations section.
- Microsoft released the Exchange Emergency Mitigation Service (EEMS) mitigation for this issue. More information is in the Mitigations section.
- Antimalware Scan Interface (AMSI) guidance, and auditing AV exclusions to optimize detection, and blocking of the Exchange vulnerability exploitation in the Detection section.
- Microsoft Sentinel hunting queries in the Detection section.
Summary
Microsoft is investigating two reported zero-day vulnerabilities affecting Microsoft Exchange Server 2013, Exchange Server 2016, and Exchange Server 2019. The first one, identified as CVE-2022-41040, is a Server-Side Request Forgery (SSRF) vulnerability, and the second one, identified as CVE-2022-41082, allows Remote Code Execution (RCE) when PowerShell is accessible to the attacker.
Currently, Microsoft is aware of limited targeted attacks using these two vulnerabilities. In these attacks, CVE-2022-41040 can enable an authenticated attacker to remotely trigger CVE-2022-41082. It should be noted that authenticated access to the vulnerable Exchange Server is necessary to successfully exploit either vulnerability.
We are working on an accelerated timeline to release a fix. Until then, we’re providing mitigations and the detections guidance below to help customers protect themselves from these attacks.
Microsoft Exchange Online has detections and mitigations to protect customers. As always, Microsoft is monitoring these detections for malicious activity and we’ll respond accordingly if necessary to protect customers.
Microsoft Security Threat Intelligence teams have provided further analysis of observed activity along with mitigation and detection guidance in a new Microsoft Security blog.
We will also continue to provide updates here to help keep customers informed.
Mitigations
Exchange Online customers do not need to take any action.
The current Exchange Server mitigation is to add a blocking rule in “IIS Manager -> Default Web Site -> URL Rewrite -> Actions” to block the known attack patterns. Exchange Server customers should review and choose only one of the following three mitigation options.
Option 1: For customers who have the Exchange Emergency Mitigation Service (EEMS) enabled, Microsoft released the URL Rewrite mitigation for Exchange Server 2016 and Exchange Server 2019. The mitigation will be enabled automatically. Please see this blog post for more information on this service and how to check active mitigations.
Option 2: Microsoft created the following script for the URL Rewrite mitigation steps. https://aka.ms/EOMTv2
Option 3: Customers can follow the below instructions, which are currently being discussed publicly and are successful in breaking current attack chains.
1. Open IIS Manager.2. Select Default Web Site.
3. In the Feature View, click URL Rewrite.
4. In the Actions pane on the right-hand side, click Add Rule(s)…
5. Select Request Blocking and click OK.
6. Add the string “.*autodiscover\.json.*\@.*Powershell.*” (excluding quotes).
7. Select Regular Expression under Using.
8. Select Abort Request under How to block and then click OK.
9. Expand the rule and select the rule with the pattern .*autodiscover\.json.*\@.*Powershell.* and click Edit under Conditions.
10. Change the Condition input from {URL} to {REQUEST_URI}
NOTE: If you need to change any rule it is best to delete and recreate it.
Impact: There is no known effect on Exchange functionality if URL Rewrite is installed as recommended.
We strongly recommend Exchange Server customers to disable remote PowerShell access for non-admin users in your organization. Guidance on how to do this for single user or multiple users is available here.
Detection and advanced hunting
For detection and advanced hunting guidance, customers should reference Analyzing attacks using the Exchange vulnerabilities CVE-2022-41040 and CVE-2022-41082.
'컴퓨터 활용(한글, 오피스 등) > 기타' 카테고리의 다른 글
| 엑셀_함수_중복 문자 삭제 (0) | 2022.10.04 |
|---|---|
| 오라클_Error_ORA_12*** (0) | 2022.10.04 |
| emacs_사용법_윈도우 관련 명령어 (0) | 2022.08.25 |
| emacs_사용법_폰트 색 변경 (0) | 2022.08.25 |
| VI, EMACS 사용법(수정중, 계속) (0) | 2022.08.24 |


